Shield for Office365TM
Protects Your Campus Against Brute Force Attacks On Microsoft O365TM IMAP Login Service
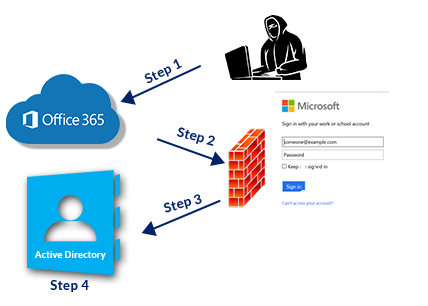
DDOS on School’s O365TM IMAP Email Protocol with both Invalid and Valid Username as MicrosoftTM does not recognize the attempts as a DDOS attack and directs the requests for login.
*QuickLaunch does not automatically block the attack because the request is coming from a valid source directly, namely MicrosoftTM
**Account lockout on Active DirectoryTM because valid Usernames are being used. This is possible because staff/student directories are typically available publicly



Procure DDOS protection service from MicrosoftTM which would filter and block ‘bad actor’ IPs
Problem gets resolved.
Cost of enabling the service.
Procure QuickLaunch Shield which would filter and block ‘bad actor’ IPs
Problem gets resolved at approximately 11% of what you would pay to MicrosoftTM annually.
Currently, this service and the blacklisting needs to be manually configured and maintained by QuickLaunch.
Note: This means that even after enabling QuickLaunch Shield, if there is an attack from a new indirect IP that isn’t on the QuickLaunch Shield global blacklist policy already, you may still experience the symptoms and be required to create a support case to allow for QuickLaunch to update its policies
This will be automated with SmartShield, which has a release date of April 30th, 2019 and will be a no-cost upgrade
Includes free upgrade to SmartShield upon GA Release
SmartShield (after April 30th, 2019) shall be at $12 / user / year
Improved Security
Identity Theft Protection
QuickLaunch Shield is a Web Application Firewall (WAF) that takes care of your account security by safeguarding you against brute force attacks on the Microsoft Office365TM IMAP protocol (ie. thick client). QuickLaunch Shield operates through a set of rules that filter malicious traffic on your Microsoft Office365TM IMAP service.
We can’t comment on why MicrosoftTM doesn’t include this service as part of its O365TM subscription, especially, considering these are direct denial-of-service-(DDOS) attacks on their IMAP protocol service.
With regards to QuickLaunch, if you are a Verify SSO customer, we have built-in DDOS detection and prevention for direct attempts and attacks to our services. However, in this case, these attempts are all indirect and through a legitimate direct source – which is MicrosoftTM – which is why our built-in DDOS services do not detect and prevent the malicious login attempts. Although, we would love to provide this solution at no additional cost to our customers, we have to invest in infrastructure and resources to develop, maintain and continue to enhance a solution that not only detects and prevents such attacks, but continues to do so automatically, intelligently, and across other services that extend beyond O365TM for a truly robust solution.
If you are already a QuickLaunch SSO customer:
With the current release, we can only blacklist by IP. In the next release, which will be called SmartShield, we will be able to do blacklisting city, state, country.
We will be releasing r2 of Shield – SmartShield – on April 30th, 2019. This release will automate the detection of malicious indirect login attempts and source IP blacklisting.
You will have to manually enable your users’ AD accounts to fix the account lock out issue.
You could try to increase your AD resources to handle the load coming from the DDOS attacks, although this may not address the performance issues.
They can be; however, if you are using QuickLaunch Adaptive Multi-Factor Authentication, all your application’s web/thin clients are protected through 2-factor verification. We recommend enabling Adaptive Multi-Factor Authentication if you haven’t done so already. Go you our pricing page for a quote.
QuickLaunch Shield is hosted in AWS.
Yes, QuickLaunch Shield can blacklist subnets.
Self-service blacklisting will be available to customers in the next upgrade with QuickLaunch SmartShield.
This will be available in the next upgrade with QuickLaunch SmartShield.